Protocols Which Use Both Asymmetric and Symmetric Cryptography
Symmetric cryptography cannot be used for exchanging secrets between machines that had never communicated before but asymmetric cryptography is limited to encrypting very small data the size of the key and is extremely slow when used to encrypt larger blocks. To do so we need to solve the following three problems.

What Is Asymmetric Encryption Dzone Security
Explain how cryptographic mechanisms can be used to guarantee the following basic security servicesi.

. Asymmetric encryption is used for keys exchange used for. But thats typically not needed for Wi-Fi because authorized users already know the password. Asymmetric encryption is more secure but is much slower to use than symmetric encryption.
Thats why all practical cryptography scheme uses both. Examples of asymmetric cryptography in everyday use include RSA the Digital Signature Standard DSSDSA and the TLSSSL protocol. The most fundamental difference between symmetric and asymmetric encryption can be summed up simply.
Many applications take advantage of the combination of symmetric and asymmetric encryption together. LEAP Lightweight Extensible Authentication Protocol Symmetric block cipher that was widely used for many years dating back to the 1970s. The best answer is that it does both.
If you want. How Does SSLTLS Encryption Work. So asymmetric is only used during the initial setup of communication.
Methodology to a wider class of protocols based on both symmetric and asymmetric cryptography. Each approach to protecting data has its benefitsespecially when applied to the appropriate scenarios. Using asymmetric cryptography to encrypt a single-use symmetric encryption key which in turn gets used to encryptdecrypt the contents of that internet browsing session Mobile chat systems.
Symmetric encryption which is used through the rest is faster and more. AES Advanced Encryption Standard Blowfish DES Data Encryption Standard Triple DES Serpent and Twofish. Abstract We present the first type and effect system for proving authenticity properties of security protocols based on asymmetric cryptography.
Now in symmetric protocols data is. Symmetric key encryption is a type of encryption that makes use of a single key for both the encryption and decryption process. TLS uses asymmetric encryption to first establish the identity of one or both parties.
Asymmetric encryption is used to establish a secure session between a client and a server and symmetric encryption is used to exchange data within the secured session. It encrypts data in 64-bit blocks. To this end we designed a cryptobiometrics system featuring the above-mentioned characteristics in order to generate cryptographic keys and the rest of the elements of cryptographic schemesboth symmetric and asymmetricfrom a biometric pattern or template no matter the origin ie face fingerprint voice gait behaviour and so on.
TLS uses both asymmetric encryption and symmetric encryption. Both protocols are a bit complicated but the crypto design is what youre after. During a TLS handshake the client and server agree upon new keys to use for symmetric encryption called session keys Each new communication.
The plaintext is encrypted to ciphertext utilising symmetric encryption to make use of speed. SSL uses asymmetric encryption to exchange keys but then switches to symmetric encryption for its lower overhead. 1 Let us say data is tainted if it may have been generated by the opponent otherwise untainted and public if it may be revealed to the opponent otherwise secret.
The use of both symmetric and asymmetric cryptography keys are part of a well-rounded solution for securing digital transactions. We denote by e_i_ i0 7 the basis of the octonion algebra mathrm O. The protocol involves communication between network entities.
Secondly it uses asymmetric encryption to exchange a key to a symmetric cipher. SSLTLS uses both asymmetric and symmetric encryption to protect the confidentiality and integrity of data-in-transit. This means that each side of the communication must have the same protocol installed to operate a successful communication between both entities.
The another two symmetric cryptographic key exchange protocols are based on the automorphism and the derivation of the octonion algebra. Some of the encryption algorithms that use symmetric keys include. Uses a relatively small key of only 56 bits and can be broken with brute force attacks.
Explain why deep packet inspection cannot be performed on protocols such as SSL and SSH. Both forms are considered secure but the level of security in any given encrypted message has more to do with the size of the keys than the form of encryption. Standing for Internet Key Exchange version 2 it actually provides key exchange for the IPsec protocol.
TLS also known as SSL is a protocol for encrypting communications over a network. This protocol uses asymmetric protocol known as SCADD protocol proposed by SHJokhio cryptography for device identification using public-private et al17 to eliminate the probabilities of node compromise key and symmetric cryptography to exchange session keys and node capture attacks in wireless sensor networks. Here we look at the reasons for using each cryptographic method.
So let us say A and B need to communicate between each other using Symmetric. When both symmetric key and asymmetric key cryptography are combined it most likely follows this methodology. How are asymmetric encryption and symmetric encryption used for TLSSSL.
Use DH to get a key and a salted hashed password transmitted under symmetric encryption for authentication. It employs asymmetric encryption in the shape of Curve22519 for the Diffie-Helman exchange and symmetric encryption for the actual transfer of data. Up to 10 cash back The first protocol is the generalization of the RSA algorithm to the octonion arithmetic 18.
Most of the protocols are symmetric. DES Data Encryption Standard Symmetric block cipher. If security is a major concern for you then you should be using end-to-end.
Using asymmetric cryptography to verify the identity of participants at the start of a conversation and then symmetric cryptography to encrypt the ongoing. Both symmetric and asymmetric encryption protocols are powerful and secure but only if they are used in the correct contexts. Key exchange in fact is one of the primary uses of asymmetric encryption.
The most significant new feature.

Symmetric Vs Asymmetric Encryption 101 Computing
15 1 Asymmetric Encryption Explained Chapter 15 Asymmetric Encryption Part Iii Net Cryptography Net Programming Security Programming Etutorials Org

Symmetric Vs Asymmetric Encryption 101 Computing

Asymmetric Key Cryptography Fig 2 Symmetric Key Cryptography Download Scientific Diagram

What Is Symmetric Key Cryptography Encryption Security Wiki
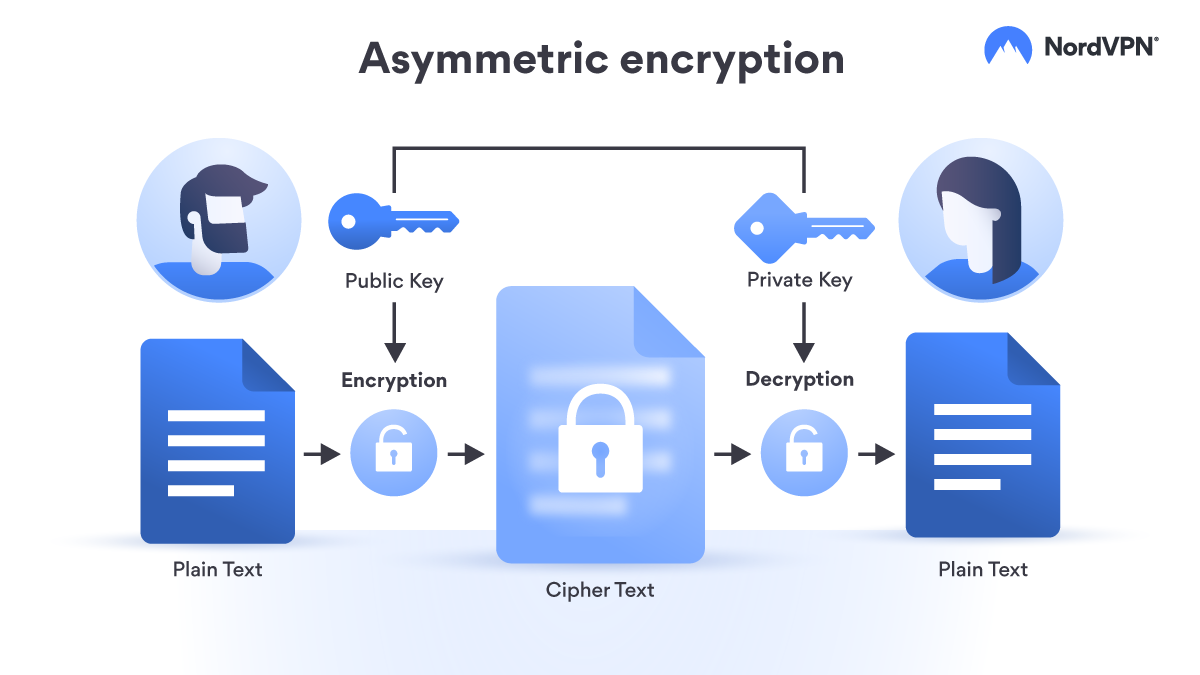
What Is Asymmetric Cryptography Nordvpn

What Is Asymmetric Encryption Dzone Security
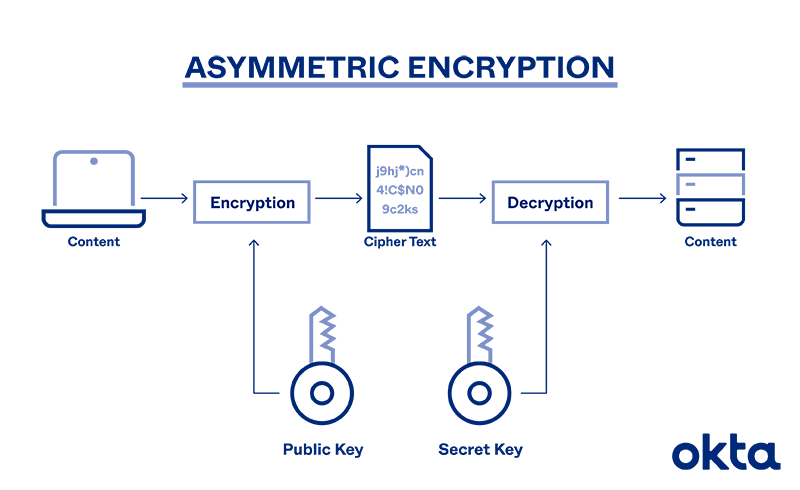
Asymmetric Encryption Definition Architecture Usage Okta

Symmetric Vs Asymmetric Encryption 101 Computing
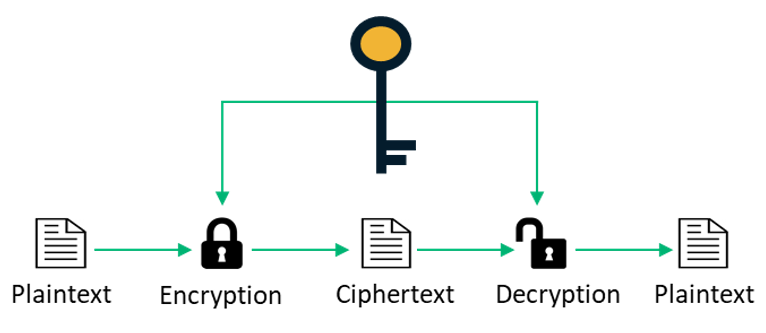
Symmetric Vs Asymmetric Encryption 5 Differences Explained By Experts
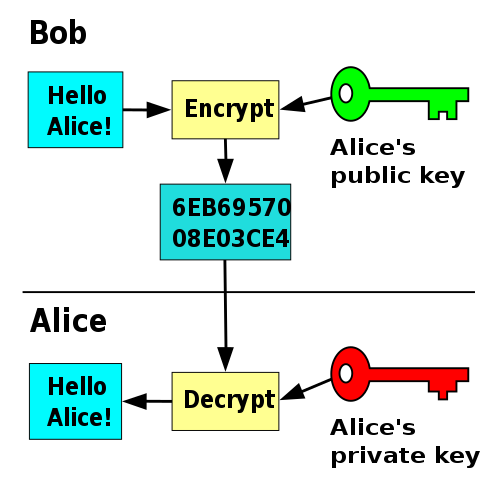
Public Key Cryptography Wikiwand
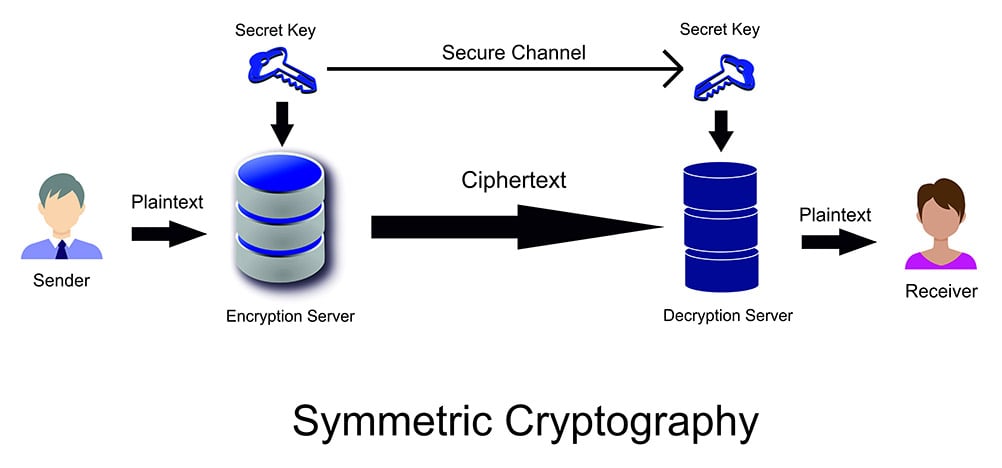
Symmetric Vs Asymmetric Encryption What S The Difference
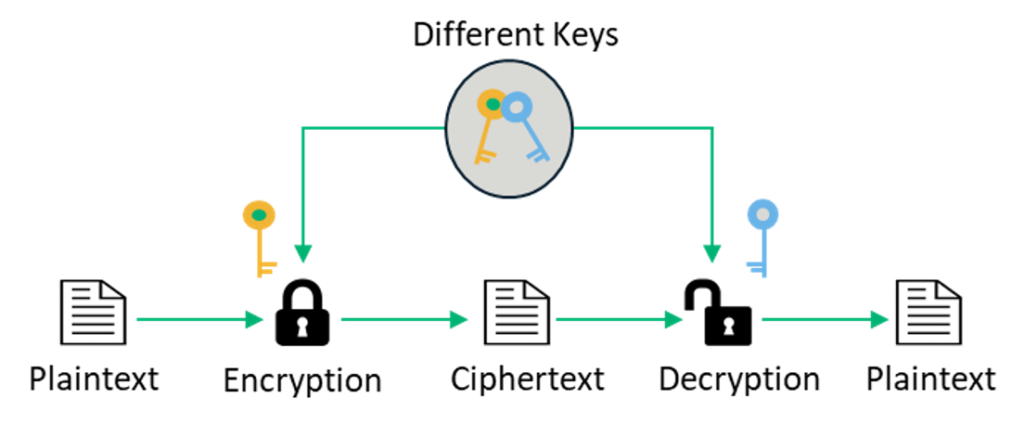
Symmetric Vs Asymmetric Encryption 5 Differences Explained By Experts

What Is Asymmetric Encryption How Does It Work Infosec Insights
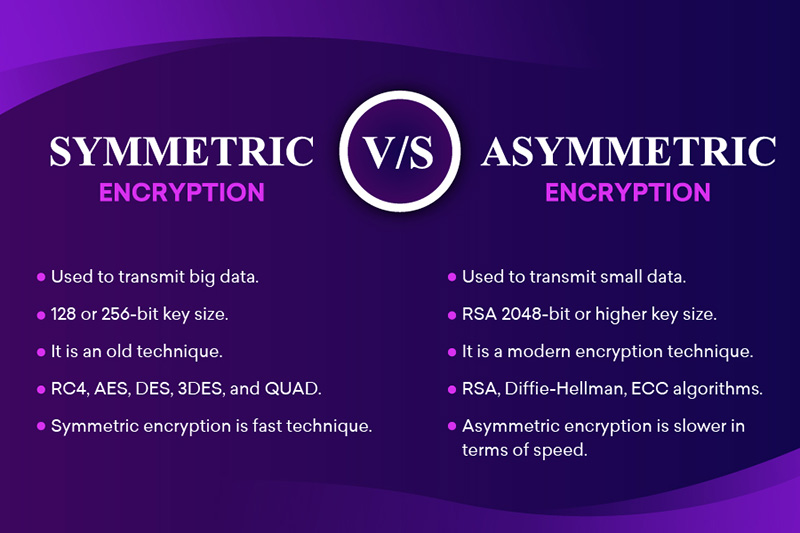
Symmetric Vs Asymmetric Encryption The World Financial Review

Asymmetric Cryptography An Overview Sciencedirect Topics

Types Of Encryption Symmetric Or Asymmetric Rsa Or Aes The Missing Report
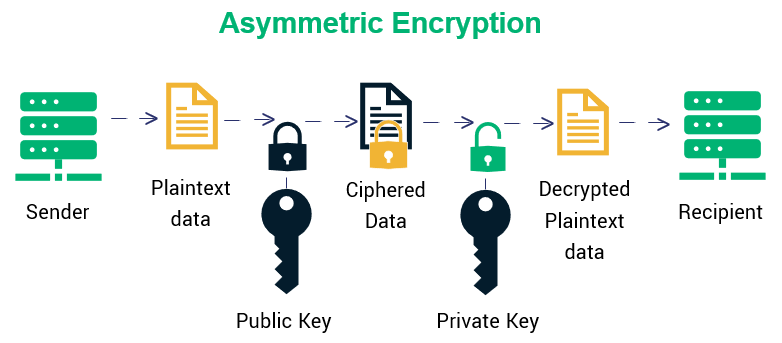
Types Of Encryption What To Know About Symmetric Vs Asymmetric Encryption Infosec Insights
